CPE Scan
About CPE
By registering CPE (Common Platform Enumeration) with FutureVuls, vulnerabilities other than OS packages can be detected.
For an explanation of CPE, please refer to IPA overview of CPE.
Two types of CPE are defined:
- URI format (example:
cpe:/a:microsoft:internet_explorer:8.0.6001:beta) - Formatted String format (example:
cpe:2.3:a:microsoft:internet_explorer:8.0.6001:beta:*:*:*:*:*:*)
The URI format is called version 2.2, and the Formatted String format is called version 2.3. The amount of information displayed does not change, only the display format differs. FutureVuls can register both URI and Formatted String formats, but only the URI format is displayed.
Uses of CPE
By using CPE, vulnerabilities in software other than package managers can be detected. For example, the following vulnerabilities can be detected:
- Firmware for network devices (e.g.
cpe:/o:cisco:ios:-) - Commercial middleware such as Oracle Database and Oracle WebLogic
- Software compiled from source by oneself
It is also possible to do the following, but methods other than CPE scanning are recommended:
- For programming language libraries, it is easier to register with Dependency Library Scan
- Scanning via a scanner is recommended for CPE scanning of OS vulnerabilities due to possible false positives
Vulnerability DB for CPE Scanning
The main vulnerability DB used for CPE scanning is NVD.
It is possible to detect vulnerabilities in Japanese-made software that are not defined in JVN, but there is a possibility of false positives. For details, please refer to Detecting vulnerabilities in Japanese-made software with JVN.
For software under package manager management, it is recommended to use scanner-based scanning instead of CPE scanning. For details, please refer to FAQ/CPE Scan.
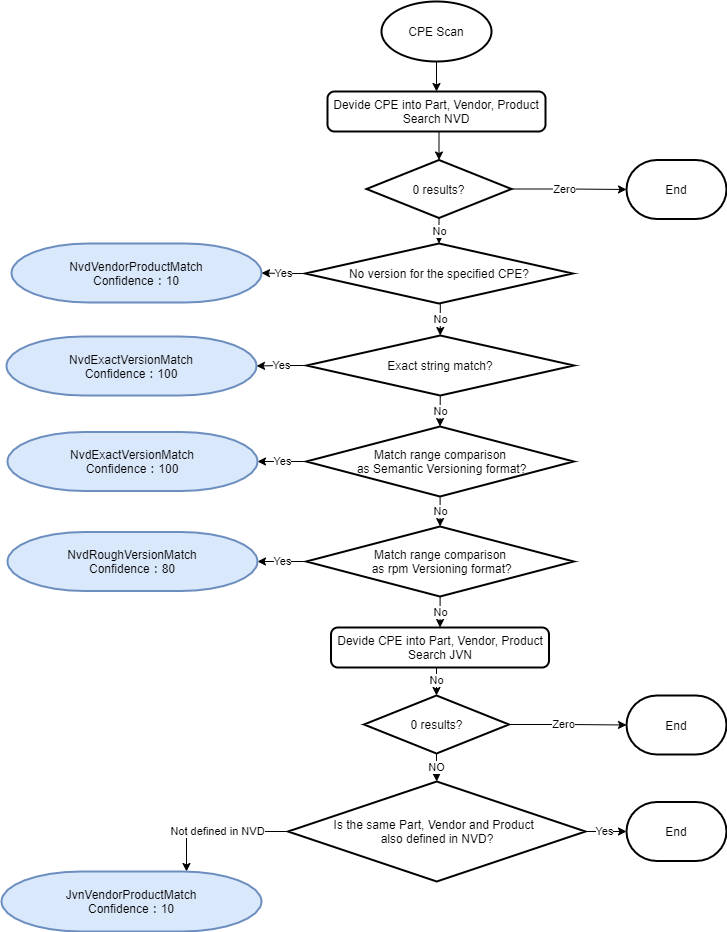
Detailed Processing for CPE Scanning
The detection process for CPE scanning is shown in detail below.
Registering CPE
CPE can be registered from Server > Software > Add CPE.
Currently, there are six ways to register CPE.

Registering CPE alone does not result in vulnerability detection. The detection process is executed when the server associated with the CPE is scanned.
When registering network equipment as CPE, please register the information corresponding to the {o=OS} category, not the {h=hardware}.
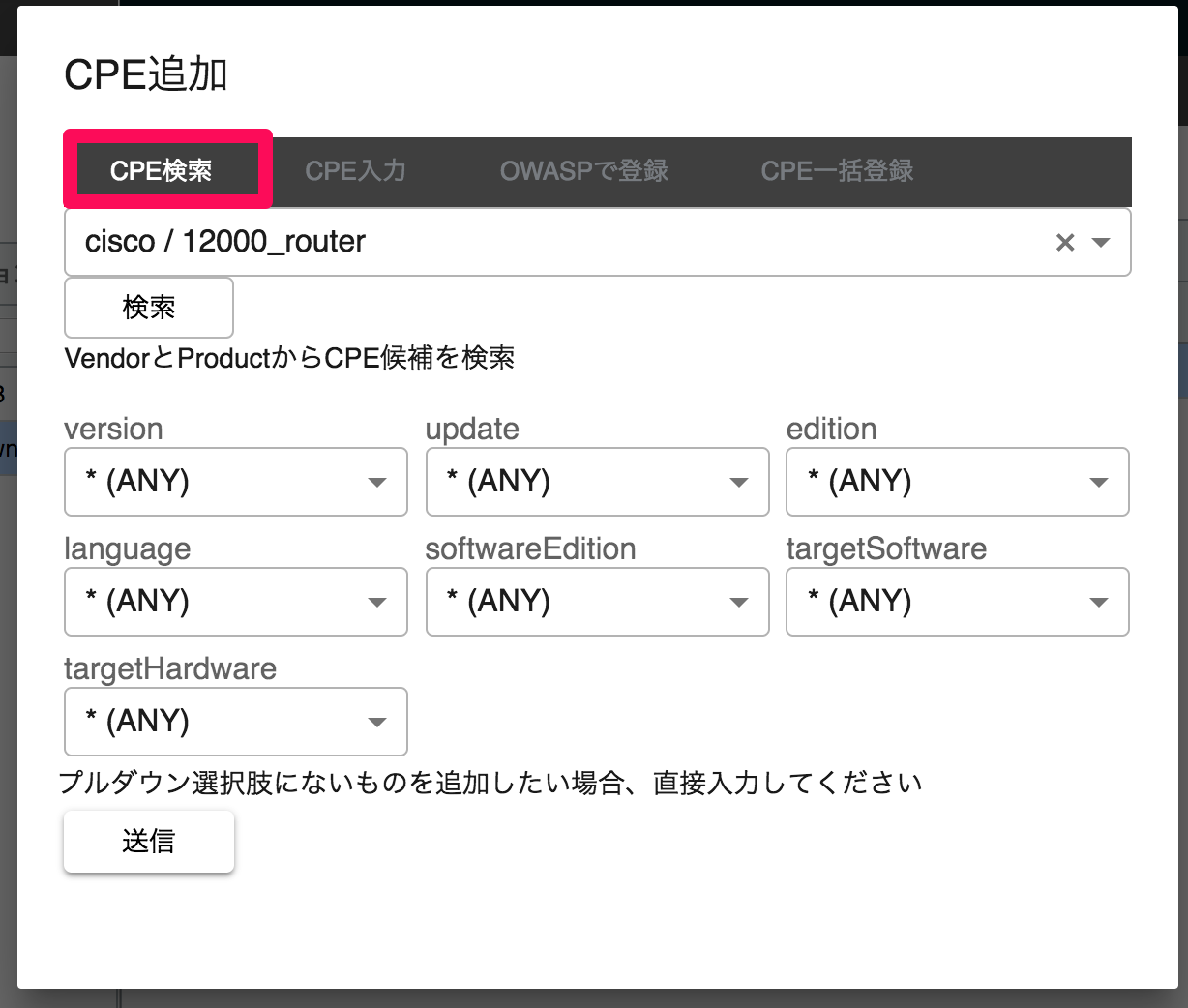
1. Register by selecting from pull-down
Register CPE by selecting from pull-down for part and vendor.
The CPE candidates that appear in the pull-down are obtained from the NVD database. If no candidate is found in the pull-down, you can also register it manually.
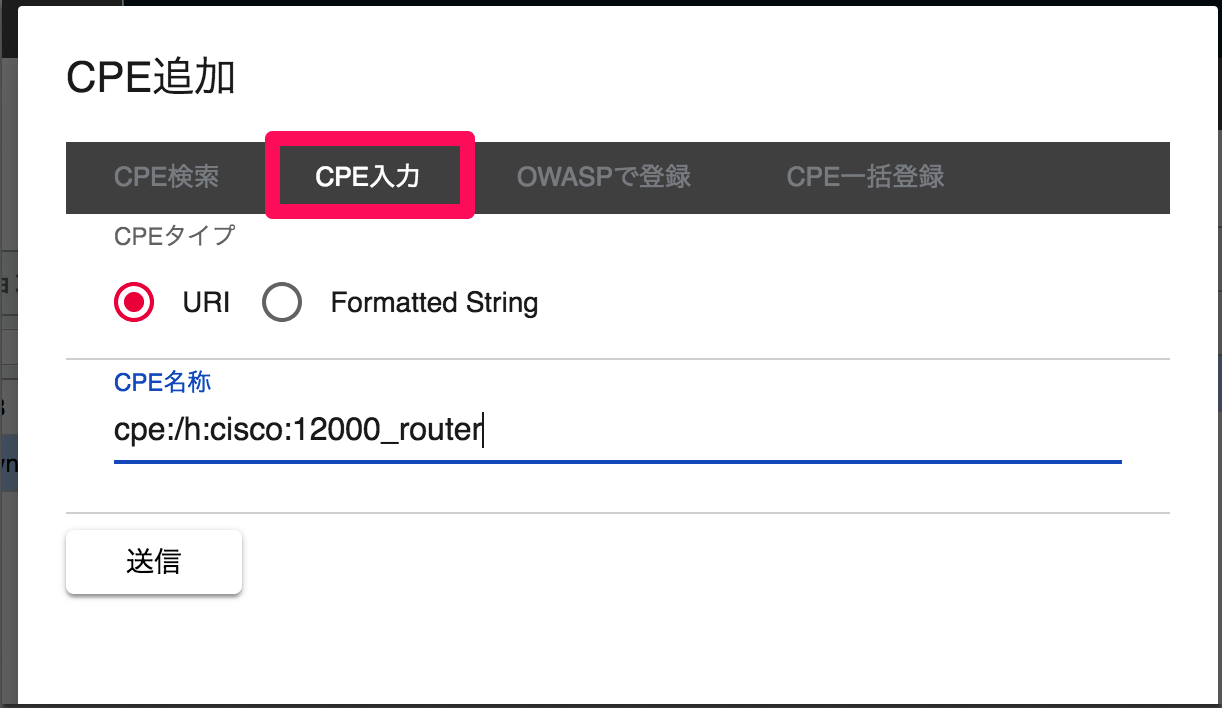
2. Register by URI or FormattedString
If you know the format of the CPE, you can register it by pasting the CPE name.
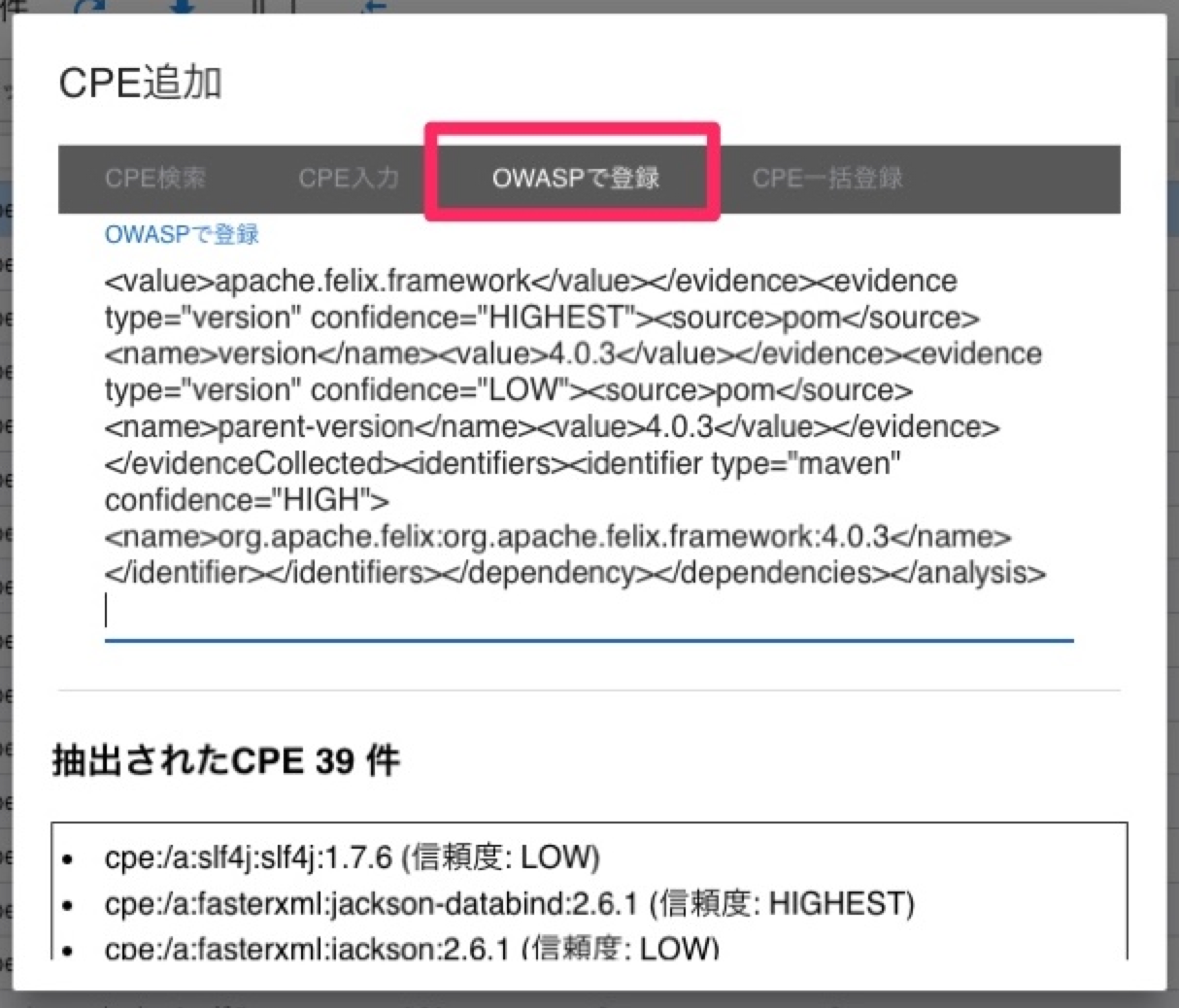
3. Register multiple CPEs from OWASP Dependency Check XML
If you are using OWASP Dependency Check, you can register the detected libraries all at once by using the outputted XML.
Please confirm again and register the CPE with low reliability.
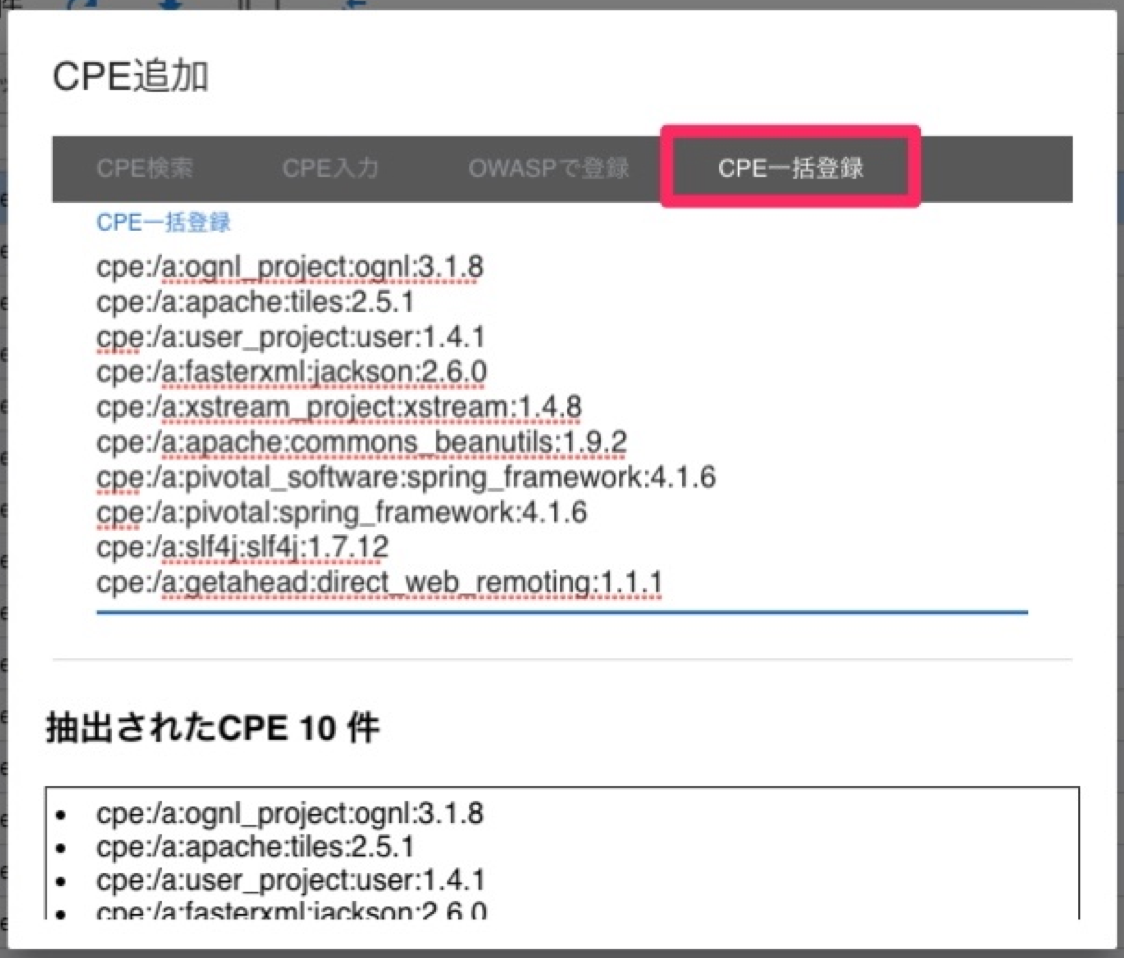
4. Register multiple CPEs with free text
If you have multiple CPEs to register, you can paste them in free text and register them.
5. Register via REST API
You can register CPEs from your own program via REST API. See documentation for details.
6. Register using the command
From acquiring the CPEs of the software used by your network devices to registering them in FutureVuls, you can use commands to do so for each network at once.
It is also recommended that you use cron or other means to execute this process on a regular basis.
Please also refer to the README for detailed usage of the command
There are three commands to use.
-
future-vuls discover -
future-vuls add-server -
future-vuls add-cpe
You can manage CPE information on a per-network basis by running them in sequence.
Installation
git clone https://github.com/future-architect/vuls.git
cd vuls
make build-snmp2cpe
make build-future-vuls
Command description and usage
future-vuls discover
This command probes for hosts in the network specified by the CIDR range and lists the responding hosts in a toml file.
The next time it is run, only the new hosts will be added as differences.
The CIDR range must be specified to execute this command.
$ ./future-vuls discover -h
discover hosts with CIDR range. The default outputFile is ./discover_list.toml
Usage:
future-vuls discover --cidr <CIDR Range> --output <Output_File> [flags]
Examples:
future-vuls discover --cidr 192.168.0.0/24 --output discover_list.toml
Flags:
--cidr string cidr range
-h, --help help for discover
--output string output file
$ ./future-vuls discover --cidr 192.168.0.0/24
Discovering 192.168.0.0/24...
New host found 192.168.0.1
New host found 192.168.0.4
New host found 192.168.0.8
Successfully wrote to ./discover_list.toml
Examples of generated toml file
["192.168.0.1"]
ip = "192.168.0.1"
uuid = ""
fvuls_sync = false
["192.168.0.4"]
ip = "192.168.0.4"
uuid = ""
fvuls_sync = false
["192.168.0.8"]
ip = "192.168.0.8"
uuid = ""
fvuls_sync = false
future-vuls add-server
This command registers only the specified hosts from the listed hosts to FutureVuls as pseudo servers.
You can specify this by rewriting the value offvuls_synctotruefor the host you want to register.
The UUID of the registeredpseudo serveris then appended to the toml file, and the next time it is run, it will register hosts that have not yet been registeredFvuls_sync = trueand satisfyuuid = "".
You will need the FutureVuls token and the URL of the RESTAPI server to execute this command
$ ./future-vuls add-server -h
Register hosts for Fvuls as a pseudo server. The default outputFile is ./discover_list.toml
Usage:
future-vuls add-server --token <VULS_TOKEN> --output <Output_File> [flags]
Examples:
future-vuls add-server --token <VULS_TOKEN> --output ./discover_list.toml
Flags:
-h, --help help for add-server
--output string output file
-t, --token string future vuls token ENV: VULS_TOKEN
--url string future vuls upload url ENV: VULS_URL
$ ./future-vuls add-server --url "https://rest.vuls.biz/v1" --token <VULS_TOKEN>
192.168.0.2: Adding to Fvuls server...
192.168.0.2: Done.
Successfully wrote to ./discover_list.toml
future-vuls add-cpe
This command executes snmp2cpe on the host registered as a pseudo-server to obtain CPE information, and then registers the CPE with FutureVuls.
The registered CPE is appended to the toml file as Formatted string format, and only the difference is registered at the next execution.
You will need the FutureVuls token and the URL of the RESTAPI server to execute this command.
If you need information about snmp2cpe, please refer to README.
$ ./future-vuls add-cpe -h
scan device CPE and upload to Fvuls. The default outputFile is ./discover_list.toml
Usage:
future-vuls add-cpe --token <VULS_TOKEN> --output <Output_File> [flags]
Examples:
future-vuls add-cpe --token <VULS_TOKEN>
Flags:
-h, --help help for add-cpe
--output string output file
--snmpVersion string snmp version v1,v2c and v3. default: v2c
-t, --token string future vuls token ENV: VULS_TOKEN
--url string future vuls upload url ENV: VULS_URL
$ ./future-vuls add-cpe --token <VULS_TOKEN> --url "https://rest.vuls.biz/v1"
Uploading CPE to https://rest.vuls.biz/v1/pkgCpe/cpe...
192.168.0.2: Done.
192.168.0.2: Found new cpe: cpe:2.3:h:fortinet:fortigate-50e:-:*:*:*:*:*:*:*
192.168.0.2: Found new cpe: cpe:2.3:o:fortinet:fortios:5.4.6:*:*:*:*:*:*:*
192.168.0.2: Upload CPE...
192.168.0.2: Done.
192.168.0.2: Successfully uploaded 2 cpes to Fvuls.
Pseudo Server
For example, if you want to scan the firmware of a network device for CPEs, you can add a Pseudo Server as an empty server and register the CPEs.
You can create a Pseudo Server from the Add Server on the server list. Once created, you can register CPEs from software like a normal server.
Please note that Pseudo Servers are also calculated as one server for pricing purposes, like scan servers.
After registering CPEs, you can perform scans on the screen to check for vulnerabilities. Pseudo servers are automatically scanned daily and can also be scanned manually.

CPE scan timing
The timing of CPE scans differs between pseudo servers and other servers.
For normal servers, the vulnerability of the CPE associated with the normal server is detected at the following timing:
- Perform manual scan on the screen
- Timing of upload from scanner
For pseudo servers, it is as follows:
- Perform manual scan on the screen
- Timing of automatic daily scan
The scan time is recorded in “Group settings > Scan history”.
Updating CPEs
Once registered, CPEs can be updated from the screen. By updating CPEs, you can receive alerts for vulnerabilities that are not detected with the previous version of the CPE.
CPEs that have been updated will be scanned automatically the next time the server is scanned.