Windows Scan
About Windows Scan
With FutureVuls, you can detect and manage vulnerabilities in Windows using both installed and uninstalled Microsoft Knowledge Base (KB) updates. CVE-IDs contained in uninstalled KB updates are detected as vulnerabilities that may exist in the client.
By converting KB to CVE, you can judge them using the same indicators as other management targets, such as Linux or libraries. You can also perform triage and response based on information such as warning information and attack codes.
Windows in any environment can be scanned, including:
- Environment that can connect to Internet Windows Update
- Environment under WSUS
- Offline environment / when scanner cannot be installed
For more information on vulnerability detection, refer to here.
Please refer to Supported Environment for scan targets.
- Windows does not currently support remote scanning. Use local scanning or PASTE scan for a closed network.
Detecting vulnerabilities using Windows Scanner
This is a method of installing a Windows scanner on the client and detecting vulnerabilities. Use this method primarily if scanner installation is possible.
Scanner installation
Refer to the tutorial for installation method.
The Windows install script uses the bitsadmin command, which is a standard HTTP client built into Windows.
Refer to Windows Scan FAQ if an error occurs during scanner installation.
Manual Scan
The Windows scanner executes scans once per day automatically using the Task Scheduler.
If you want to run the scanner immediately after installation or at any other time, follow these steps:
- Method 1Run from the Task Scheduler
- Method 2Run from the Command Prompt
Run from the Task Scheduler
- Open the Task Scheduler
- Select
vuls-saasand [Right click][to execute]

Running from the command prompt
To run a scan manually, execute the following command as an administrator:
C:\Program files\vuls-saas\vuls-saas.bat
If scan results are not reflected
After the scan is finished, it will be reflected on the web page after a while.
If the results are not reflected even after waiting for 10 minutes, check the following log file to find out the cause:
C:\Program Files\vuls-saas\vuls-windows.log- This file contains information about the success or failure of the scan and upload.
- If the scan fails, the report information will not be uploaded to FutureVuls.
If an error occurs, refer to the Windows Scan FAQ.
Customize the information to upload
You can filter the information you want to upload to FutureVuls by specifying the JSON key of the information you do not want to upload in IgnoredJSONKeys in config.toml.
- Sample: Do not upload a list of installed applications.
[Servers]
[Servers.localhost]
Host = "localhost"
UUID = "xxx-xxx-xx"
IgnoredJSONKeys = ["packages"]
To confirm the JSON key to specify in config.toml, execute vuls.exe with the following procedure or you can refer FAQ.
- Add debug flag and execute vuls.exe
C:\Program Files\vuls-saas>vuls.exe -debug
- Check json file created under results directory on the editor tool
Checking the scan results
The scan results obtained by executing the scanner are automatically deleted after being uploaded to FutureVuls.
If you want to keep the file, run the scanner with the -debug flag from the command prompt.
C:\Program Files\vuls-saas>vuls.exe -debug
If there are detection omissions in the scan results
If there are detection omissions for applied or unapplied update packages, check the list of advisories and use the manual KBID manual registrationto supplement them.
Scanning Windows under WSUS
You can detect unapplied KBs by referring to the WSUS on the local network by configuring config.toml.
To change the destination of Windows Update access, set WinUpdateSrc in config.toml as follows:
- Specify “2” for Windows Update on the Internet (default).
[Servers]
[Servers.localhost]
Host = "localhost"
UUID = "xxx-xxx-xx"
WinUpdateSrc = "2"
- Specify “1” for local WSUS
[Servers]
[Servers.localhost]
Host = "localhost"
UUID = "xxx-xxx-xx"
WinUpdateSrc = "1"
If Windows scan under WSUS does not work properly, please refer to the following:
PASTE scan
By registering the KBIDs related to updated programs that have been applied or not applied to Windows on the FutureVuls screen, vulnerabilities can be detected without using a scanner.
Supports environments where FutureVuls scanner is difficult to introduce, such as:
- Isolated from the Internet
- Environments where scanner programs cannot be installed on the server
In addition, if there is a detection omission in the updated program detected by scanner, it can be complemented using the PASTE scan function.
Please refer to the supported environment for the target of PASTE scan.
New registration
To perform a new PASTE scan on Windows, follow these steps:
- Click
Add server>Add PASTE serverin the server, open the dialog - Enter the server name
- Copy and execute the displayed command in PowerShell
- Paste and send the result of 3. from the FutureVuls screen
Add PASTE server

Enter server name

Paste installed update program information

After registration, the scan will be automatically executed, and vulnerabilities will be detected by complementing the unapplied update program. If you want to manage vulnerabilities more strictly, use the manual registration of KBID function to register unregistered update program information.
Manual registration of KBID
If there are updates or deficiencies in the KB information registered by PASTE scan, please manually register the KBID using this function. You can also use it if there are deficiencies in the KB information registered by the Windows scan with the scanner.
- Click the server to be managed on the server tab, and open the advisory tab from the second pane.
- Enter all KBIDs indicating updated programs applied/unapplied to Windows from
KBID registrationand send. - When you execute Manual Scan, unapplied update patches and associated vulnerabilities are automatically detected.
- If you try to register a KBID that is already registered, an error occurs.
- If the target KBID was manually registered, delete the KBID, perform Manual Scan, and then register it again.
- If the target KBID was automatically registered from other manually registered KBIDs, delete the base KBID, perform Manual Scan, and then register it again.
- In Windows PASTE Scan, unapplied update patches are automatically detected from the registered applied update patches. You can directly register unapplied update patches from
KBID registration, but it is not recommended because it increases the risk of false detection. - The KBID detected by the scanner always takes precedence over the manually registered KBID. If the KBID manually added and the KBID detected by the scanner are the same but have different application statuses, the KBID detected by the scanner is used to detect vulnerabilities. A warning message is displayed in the scan history, so delete the manually registered KBID.
Obtaining applied/unapplied update patches (KBIDs) on Windows
Here are three methods to obtain applied/unapplied update patches (KBIDs) on Windows.
| Method of obtaining KBIDs | Applied | Unapplied |
|---|---|---|
| Windows Update API (CUI) | ✅ | ✅ |
| Windows settings > Update & Security > Windows Update (GUI) | ✅ | ✅ |
| Get-HotFix (CUI) | ✅ | ❌ |
Windows Update API
The feature of this method is that you can get the same result as the scanner even in an environment isolated from the Internet by preparing wsusscn2.cab. In addition, it supports obtaining unapplied KBIDs and can format the execution result into an easy-to-register KBID, so it is recommended.
Execute the following command in PowerShell.
- For environments where Windows Update cannot be connected online (such as those isolated from the Internet)
# Download http://download.windowsupdate.com/microsoftupdate/v6/wsusscan/wsusscn2.cab in advance.
PS C:\Program Files\vuls-saas> $applied = @()
PS C:\Program Files\vuls-saas> $unapplied = @()
PS C:\Program Files\vuls-saas> $Session = New-Object -ComObject Microsoft.Update.Session
PS C:\Program Files\vuls-saas> $ServiceManager = New-Object -ComObject Microsoft.Update.ServiceManager
PS C:\Program Files\vuls-saas> $UpdateService = $ServiceManager.AddScanPackageService("Offline Sync Service", "C:\Program Files\vuls-saas\wsusscn2.cab", 1)
PS C:\Program Files\vuls-saas> $UpdateSearcher = $Session.CreateUpdateSearcher()
PS C:\Program Files\vuls-saas> $UpdateSearcher.WinUpdateSrc = 3
PS C:\Program Files\vuls-saas> $UpdateSearcher.ServiceID = $UpdateService.ServiceID
PS C:\Program Files\vuls-saas> foreach($e in $UpdateSearcher.QueryHistory(0, $UpdateSearcher.GetTotalHistoryCount())){ If ($e.Title -match '(KB\d{6,7})') { $applied += $Matches[0] }}
PS C:\Program Files\vuls-saas> foreach($e in $UpdateSearcher.search("IsInstalled=1 and RebootRequired=0 and Type='Software'").Updates){ $applied += ('KB'+$e.KBArticleIDs) }
PS C:\Program Files\vuls-saas> foreach($e in $UpdateSearcher.search("IsInstalled=0 and Type='Software'").Updates){ $unapplied += ('KB'+$e.KBArticleIDs) }
PS C:\Program Files\vuls-saas> foreach($e in $UpdateSearcher.search("IsInstalled=1 and RebootRequired=1 and Type='Software'").Updates){ $unapplied += ('KB'+$e.KBArticleIDs) }
PS C:\Program Files\vuls-saas> ($applied | Select-Object -Unique) -Join ',' # AppliedKBID
KB5011651,KB5012599
PS C:\Program Files\vuls-saas> ($unapplied | Select-Object -Unique) -Join ',' # Inapplied KBID
KB5012117
- For environments where online connection to Windows Update is possible (such as environments where the scanner program cannot be installed on the server).
PS C:\Program Files\vuls-saas> $applied = @()
PS C:\Program Files\vuls-saas> $unapplied = @()
PS C:\Program Files\vuls-saas> $Session = New-Object -ComObject Microsoft.Update.Session
PS C:\Program Files\vuls-saas> $UpdateSearcher = $Session.CreateUpdateSearcher()
PS C:\Program Files\vuls-saas> $UpdateSearcher.WinUpdateSrc = 1 # or 2
PS C:\Program Files\vuls-saas> foreach($e in $UpdateSearcher.QueryHistory(0, $UpdateSearcher.GetTotalHistoryCount())){ If ($e.Title -match '(KB\d{6,7})') { $applied += $Matches[0] }}
PS C:\Program Files\vuls-saas> foreach($e in $UpdateSearcher.search("IsInstalled=1 and RebootRequired=0 and Type='Software'").Updates){ $applied += ('KB'+$e.KBArticleIDs) }
PS C:\Program Files\vuls-saas> foreach($e in $UpdateSearcher.search("IsInstalled=0 and Type='Software'").Updates){ $unapplied += ('KB'+$e.KBArticleIDs) }
PS C:\Program Files\vuls-saas> foreach($e in $UpdateSearcher.search("IsInstalled=1 and RebootRequired=1 and Type='Software'").Updates){ $unapplied += ('KB'+$e.KBArticleIDs) }
PS C:\Program Files\vuls-saas> ($applied | Select-Object -Unique) -Join ',' # 適用済みKBID
KB5011651,KB5012599
PS C:\Program Files\vuls-saas> ($unapplied | Select-Object -Unique) -Join ',' # 未適用KBID
KB5012117
Windows Settings > Update & Security > Windows Update
The feature of this method is that you can obtain KBID without executing any commands. However, if there are a large number of applied or unapplied KBIDs, there will be a lot of input work on the KBID registration screen.
From “Windows Settings”, click on “Update & Security”.
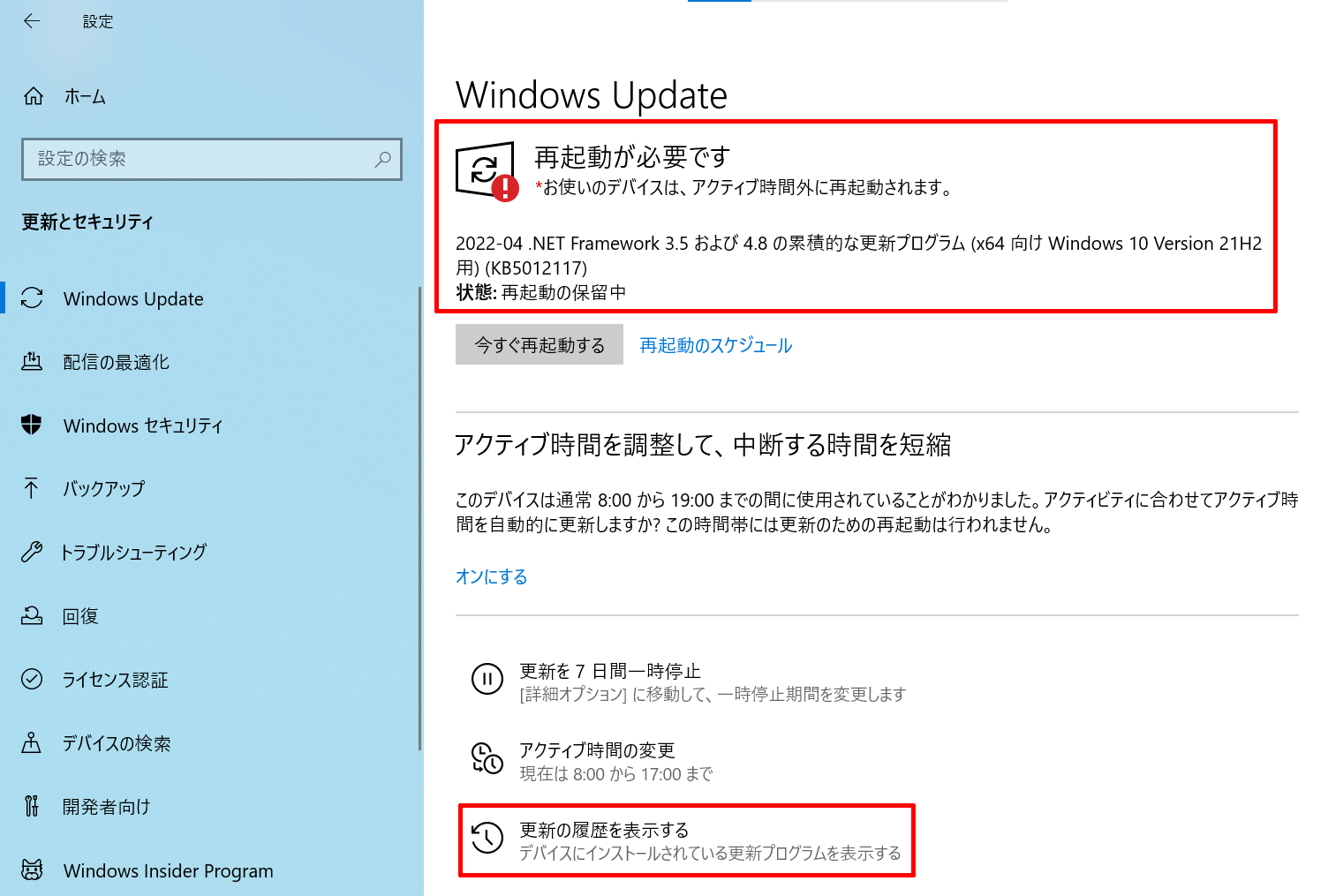
Look at “Windows Update” in “Update & Security”. The red frame at the top displays the unapplied update programs, so extract the KBID from the title of the update program. In this image, “KB5012117” is the unapplied KBID from “2022-04 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows 10 Version 21H2 for x64-based Systems (KB5012117)”. Also, when you click “View update history” in the red frame at the bottom, the title and date of the applied update program are displayed.
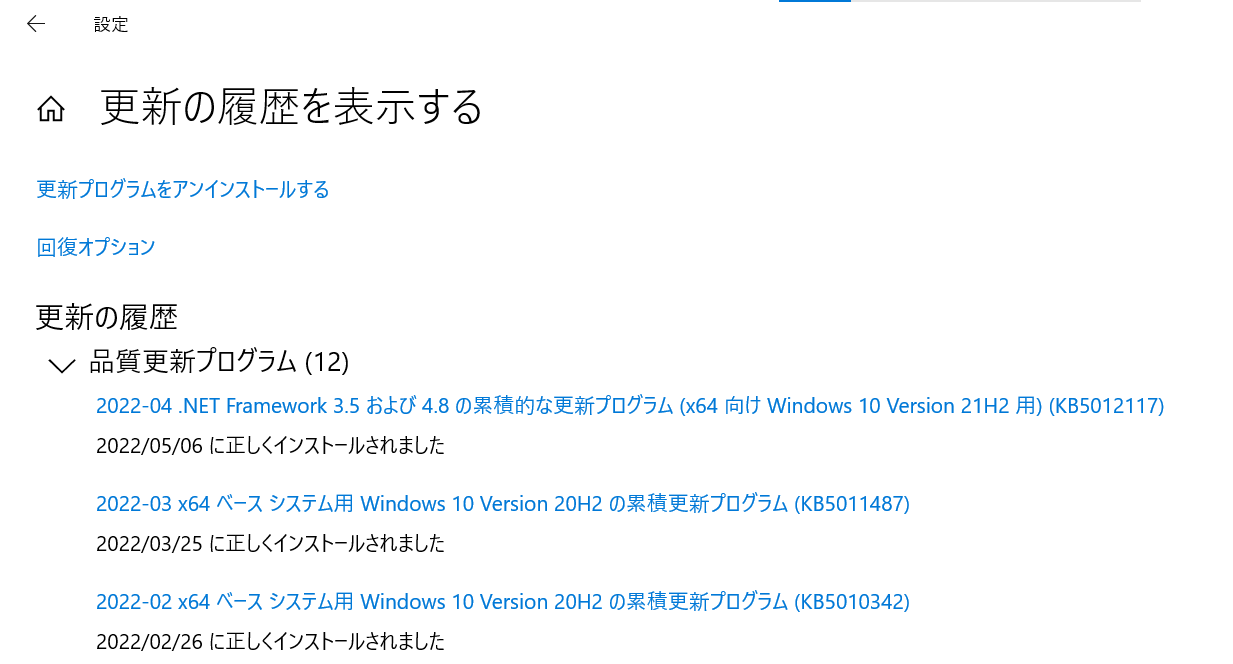
Similarly, obtain the applied KBID from the title of the update program displayed in “View update history”.
Get-HotFix
Please refer to this method when neither of the above two methods can be used. Note that unapplied KBIDs cannot be obtained with this method.
Run the following command in PowerShell.
PS C:\Program Files\vuls-saas> (Get-HotFix | Select-Object HotFixID | % { If ($_ -match '(KB\d{6,7})') { $Matches[0] }}) -Join ','
KB5012117,KB4562830,KB5003791,KB5007401,KB5012599,KB5011651,KB5005699
3.2. Register the obtained KBID.
Register the obtained applied/unapplied KBID by the method shown in 3.1.

Method for deleting KBID
If there are any updates in the Windows status, please delete the registered KBID manually.
- Click on the managed server in the Server tab and open the Advisory tab from the second pane.
- Click on the advisory you want to delete and open the third pane.
- Click the trash can icon to delete the KBID.
- When you run themanual scan unapplied update programs that were automatically detected based on the deleted update program will be removed.
- Only manually registered KBIDs can be deleted.
Windows Vulnerability Information
For Windows, vulnerability information is displayed using Microsoft’s vulnerability database.

The Microsoft vulnerability database may include Workaround information. Workaround information is displayed in the vulnerability details summary.
KBID Information
KBID is displayed as an advisory. Advisories can be confirmed in Advisory List and other places.
Installed Applications
Installed applications on Windows machines managed by FutureVuls are displayed in the Software tab. This includes applications that you have installed yourself.

