Vulnerability
About the Vulnerability Tab
The vulnerability tab displays a list of vulnerabilities detected within a group. It extracts items frequently referenced during response triage and displays them in a table, enabling efficient triage work by sorting or filtering high-risk vulnerabilities to register as tasks or hiding low-risk vulnerabilities. Its screen configuration enables batch updates of multiple selected tasks, further increasing triage efficiency.
Vulnerability List
The vulnerability list enables you to view the detected vulnerabilities in a list.
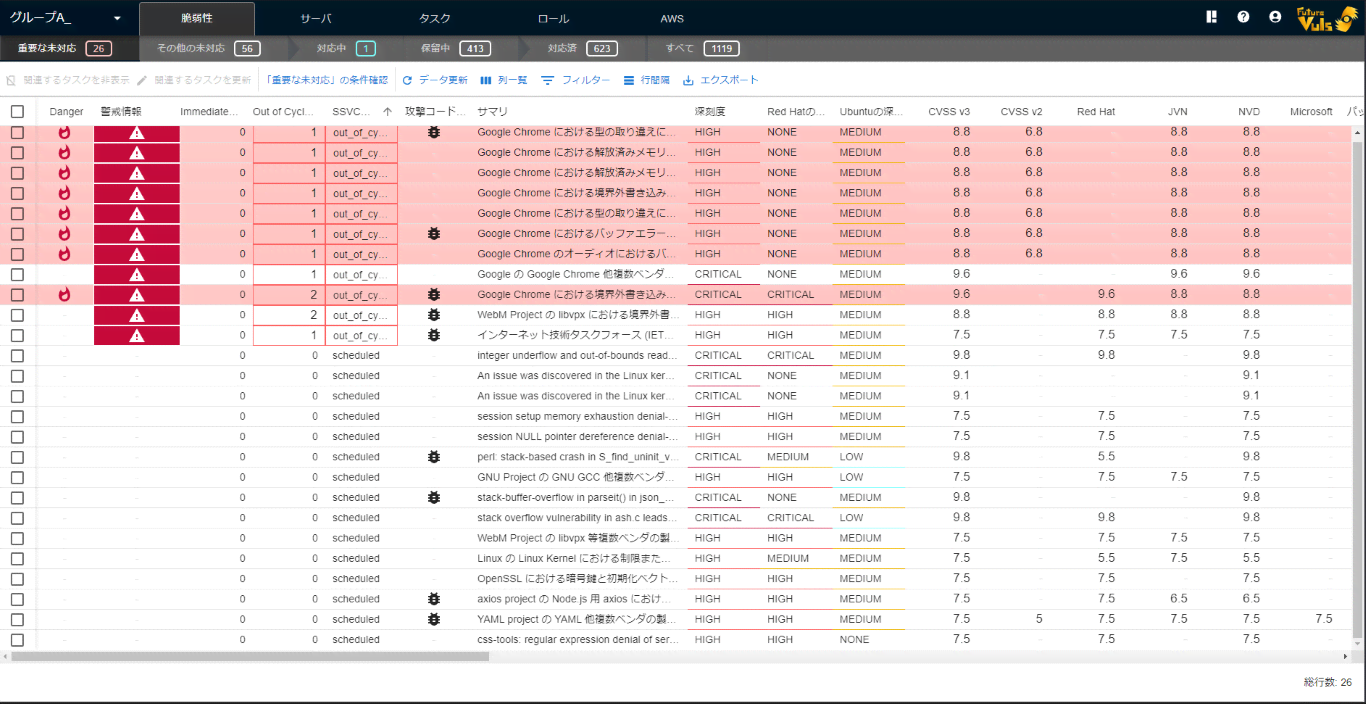
You can customize the column order and display settings for the list.
| Item | Details | Update Timing |
|---|---|---|
| CVE ID | The CVE ID of the detected vulnerability. | At Scan |
| Severity | The severity of the vulnerability, displayed as Critical, High, Low, or None based on the value of CVSSv3. |
When DB information changes |
| Summary | The summary of the vulnerability. If the language setting is ja, the summary of JVN will be displayed preferentially. |
When DB information changes |
| CVSS v2 | The maximum score of CVSSv2. | When DB information changes |
| CVSS v3 | The maximum score of CVSSv3. | When DB information changes |
| NVD | The score of NVDv3 is displayed. | When DB information changes |
| JVN | The score of JVNv3 is displayed. | When DB information changes |
| Red Hat | The score of Red Hatv3 is displayed. | When DB information changes |
| Microsoft | The score of Microsoftv3 is displayed. | When DB information changes |
| Advisory ID | The advisory ID associated with the CVE ID. (For Windows, KBID) | When DB information changes |
| Attackable from NW | Whether AV (Attack Vector) of the CVSS metric is Network. | When DB information changes |
| Attackable without privileges | Whether Au (Access Complexity) or PR (Privileges Required) of the CVSS metric is unnecessary. | When DB information changes |
| Attack code exists | Whether an attack code or PoC has been disclosed. | When DB information changes |
| Danger | Indicates if the vulnerability has the Danger flag set. | When the Danger flag is updated |
| Process is running | Whether the related process is running on the server, or if the port is open and listening. | At Scan |
| Mitigation/Evasion measures | Whether there are mitigation or evasion measures in Red Hat and Microsoft data sources. | When DB information changes |
| Alert information | Whether alert information has been published by CISA-KEV, JPCERT/CC-Alerts, and US-CERT-Alerts. CISA-KEV: Alert Information (Fatal) JPCERT/CC-Alerts、US-CERT-Alerts:Alert Information(Fatal) |
When DB information changes |
| Patch | Indicates whether there is a patch available for related vulnerable software. ✓: Valid patches for all related software are available. ☓: No patches are currently available for all related software. △: Among related multiple software, some have patches available and some don’t. ❔: There are some related software for which patch availability is unknown. -: The associated software has been patched and the vulnerability has been resolved. | When DB information changes |
| OWASP TOP10 | Indicates whether the vulnerability corresponds to OWASP TOP10. | When DB information changes |
| Total task count | Total number of tasks associated with the vulnerability. | When scanning |
| Unresolved task count | Number of tasks associated with the vulnerability whose status is “NEW” and has no hidden setting. | When scanning, or when updating tasks |
| In progress task count | Number of tasks associated with the vulnerability whose status is “INVESTIGATING”, “ONGOING”, or “DEFER”, and has no hidden setting. | When scanning, or when updating tasks |
| Resolved task count | Number of tasks associated with the vulnerability whose status is not “NEW”, “INVESTIGATING”, “ONGOING”, or “DEFER”, or has a hidden setting. | When scanning, or when updating tasks |
| CloudOne status | CloudOne integration status. | When scanning |
| Alert tags | Special alert tags registered for the vulnerability. | When alert tags are updated |
| Topic count | Number of topics registered for the vulnerability. | When updating topics |
| First detected date and time | Date and time when the CVE was first detected in the group. | When scanning |
| Latest detection date and time | Latest date when the CVE was detected in the group. | When scanning |
| Vector/Score updated date and time | Date and time when CVSS vector or score was updated or when the vulnerability was first detected. | When scanning |
| Latest topic update date and time | Latest date when a topic for the CVE was registered/updated. | When updating topics |
| Immediate unresolved task count | Number of tasks associated with the vulnerability whose SSVC priority is Immediate and status is “NEW”, and has no hidden setting. | When scanning |
| Out-of-cycle unresolved task count | Number of tasks associated with the vulnerability whose SSVC priority is Out-of-cycle and status is “NEW”, and has no hidden setting. | When scanning |
| External Scan | Whether there are any externally exposed vulnerabilities | When [add and update external scan result](/en/manual/scanimport/#Adding External Scan Results) |
Subtab
In the vulnerability list, tabs are provided to switch the display for each status of related tasks.
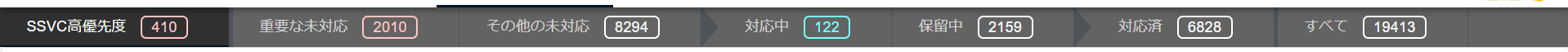
- Critical Unresolved
- Displays vulnerabilities that include unresolved tasks that meet the conditions for critical unresolved.
- Other Unresolved
- Displays vulnerabilities that include unresolved tasks that do not meet the conditions for critical unresolved.
- In Progress
- Vulnerabilities in which all related tasks have a status of
ONGOINGorINVESTIGATING.
- Vulnerabilities in which all related tasks have a status of
- Deferred
- Vulnerabilities in which all related tasks have a status of
DEFER.
- Vulnerabilities in which all related tasks have a status of
- Resolved
- Vulnerabilities for which all related tasks are set to
HIDDEN. - Vulnerabilities for which all related tasks have a status of
WORKAROUND,NOT_AFFECTED,RISK_ACCEPTED, orPATCH_APPLIED.
- Vulnerabilities for which all related tasks are set to
- All
- Displays all detected vulnerabilities.
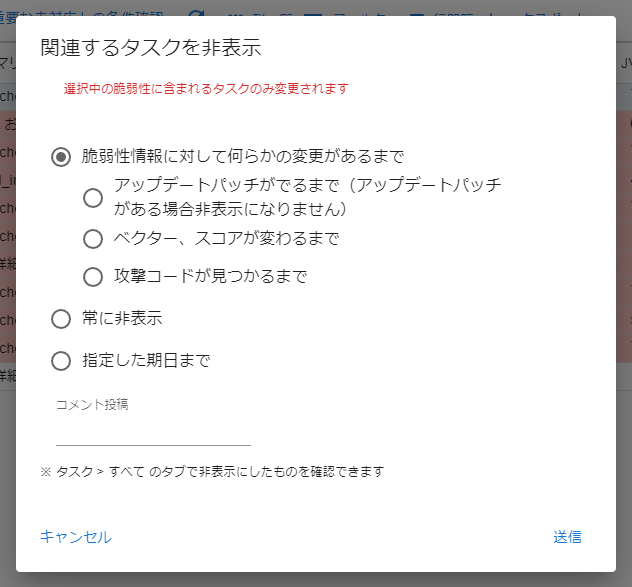
Hide tasks related to specified vulnerabilities
Select multiple vulnerabilities to hide all tasks related to those vulnerabilities on all servers.
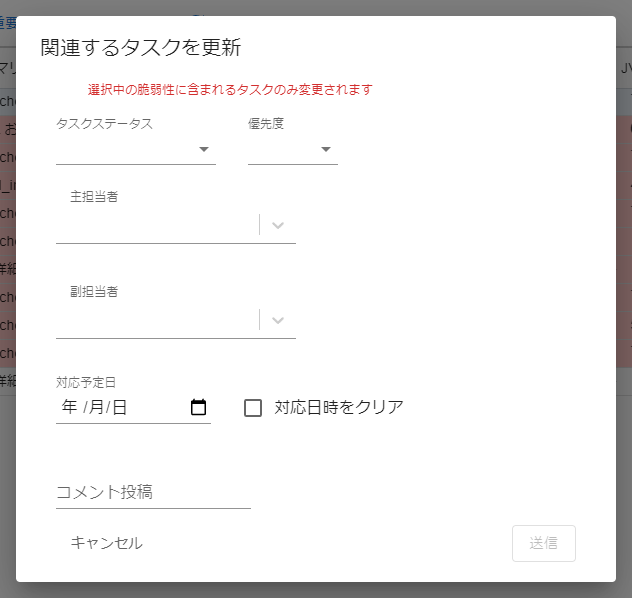
Update tasks related to specified vulnerabilities
Select multiple vulnerabilities to update all tasks related to those vulnerabilities on all servers.
Conditions for Critical Unresolved
By setting the conditions for vulnerabilities that are judged to be high risk in advance, you can prioritize dealing with vulnerabilities that meet those conditions by categorizing them in the “Critical Unresolved” tab when they are newly detected.
Only group administrators can change the conditions that categorize vulnerabilities in the “Critical Unresolved” tab.
Changes can be made in the group settings’ “Critical Filter.”
You can check the set conditions from the “Critical Filter Check” button.
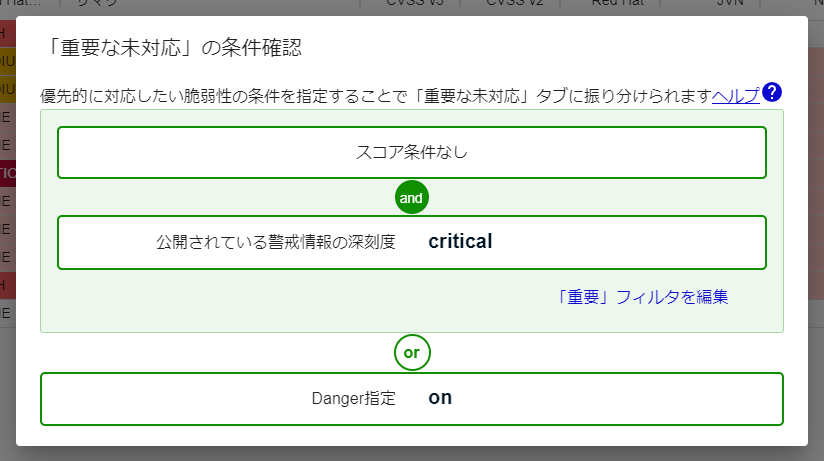
Critical Filter Items
-
CVSS Score
- Judged by the “OR” condition.
- Red Hat and Microsoft adopt the higher score of CVSS v2 or v3.
-
CVSS Base Metrics
- Judged by the “AND” condition.
- If any of the CVSSv3 metrics from each data source apply, it will be adopted. For example, if the AV (Attack Vector) is “N” for network attack, it will be judged as “AV:N.”
-
Severity of publicly disclosed warnings
- Select whether to categorize vulnerabilities in the “Critical Unresolved” tab based on the warning information for the vulnerability.
- There are three choices:
- Categorize vulnerabilities with warning information from CISA-KEV in the “Critical Unresolved” tab only.
- Categorize vulnerabilities with warning information from CISA-KEV, JPCERT/CC-Alerts, and US-CERT-Alerts in the “Critical Unresolved” tab.
- Categorize all vulnerabilities in the “Critical Unresolved” tab.
-
Vulnerabilities with low detection reliability
- Choose whether to classify vulnerabilities with low detection reliability as “important unresolved” tab.
-
SSVC Priority
- Determined by an OR condition.
- Choose whether to classify vulnerabilities based on SSVC priority as “important unresolved” tab.
Vulnerabilities specified as Danger will always be classified as “important unresolved”.
Vulnerability Second Pane
Clicking on a vulnerability item in the list will display the second pane.
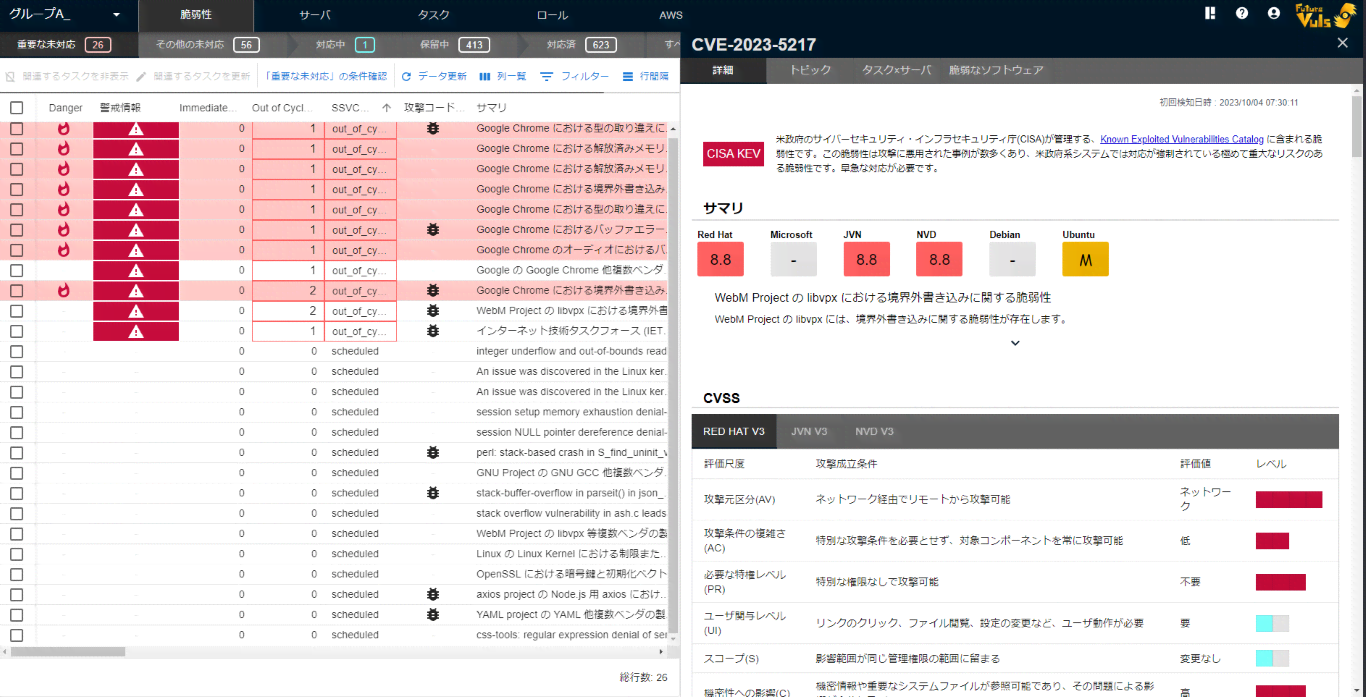
Detail Tab
In the Detail tab, you can check the details of the vulnerability.
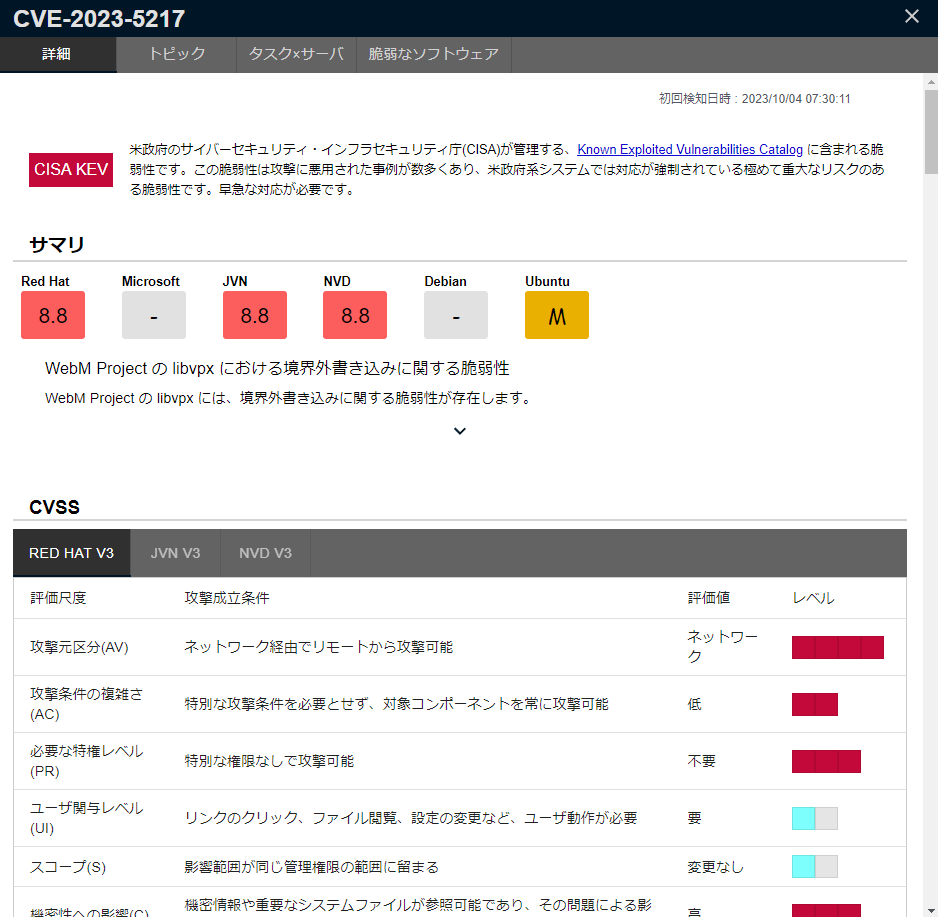
In the vulnerability details, the following items are displayed.
| Item | Details |
|---|---|
| Summary | Displays descriptions and scores of vulnerabilities from various vulnerability databases, such as NVD, JVN, Redhat, and Microsoft. |
| CVSS | Displays detailed metrics of the CVSS (v2, v3) decomposed from each vulnerability database’s vectors. |
| Exploit Code | Displays a link and description if exploit code is found. |
| Alert Information | Displays links to alert information from CISA-KEV, JPCERT/CC-Alerts, and US-CERT-Alerts if found. |
| CWE | Displays the CWE related to the vulnerability. |
| Distribution Support Pages | Displays the official vulnerability information page issued by each distribution. |
| Reference | Displays the references related to the vulnerability. |
CVSS Score Recalculation
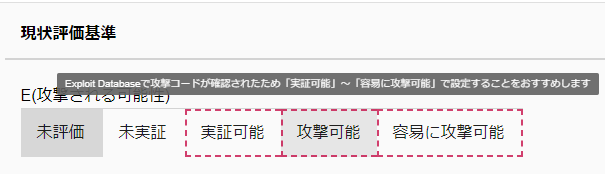
Clicking on “CVSS Score Recalculation” under CVSS will open a page for recalculation. The current value score and the score evaluated with the current value and environmental values are displayed.

In the case of vulnerabilities for which the attack code has been disclosed, a hint is displayed in a red frame under “Current Evaluation Criteria” > “Possibility of Attack”.
Topic
In FutureVuls, topics can be created for each vulnerability, allowing investigation results and comments to be shared within a group or organization.
For more information on topics, please seehere.
Tasks x Servers
Tasks and servers related to the selected vulnerability are displayed. Only “Not yet addressed” or “In progress” tasks are displayed, and tasks that have been addressed or hidden are not displayed.
Software
All installed software on servers related to the selected vulnerability can be displayed.