Software
About Software
Software includes server packages and registered CPEs. All software displayed in FutureVuls is information associated with servers. In addition, OSS licenses of application-dependent libraries such as Lockfile and Jar are detected and displayed in a list.
Software (OS Package, CPE, Library Package, Github Package)
All detected software can be checked in FutureVuls, regardless of the presence of vulnerabilities.
Also, when using fast-root to scan, the confirmation of new versions of software can be done.
CPE
CPE can be managed by manually registering them on the FutureVuls screen. In FutureVuls, CPE is displayed in URI format (registration is also possible in 2.3 format string format).
When registering CPE, it is necessary to select a server. If you want a new server dedicated to CPE, you can register it by creating a pseudo server.
For more information about CPE, see here.
Software List
The software list can be displayed from the second pane of servers, roles, and vulnerabilities.
- Server List > Software
- Only software related to the specified server is displayed.
- Role List > Software
- Only software related to the servers belonging to the specified role are displayed.
- Vulnerability List > Software
- Only software related to the specified vulnerability is displayed.
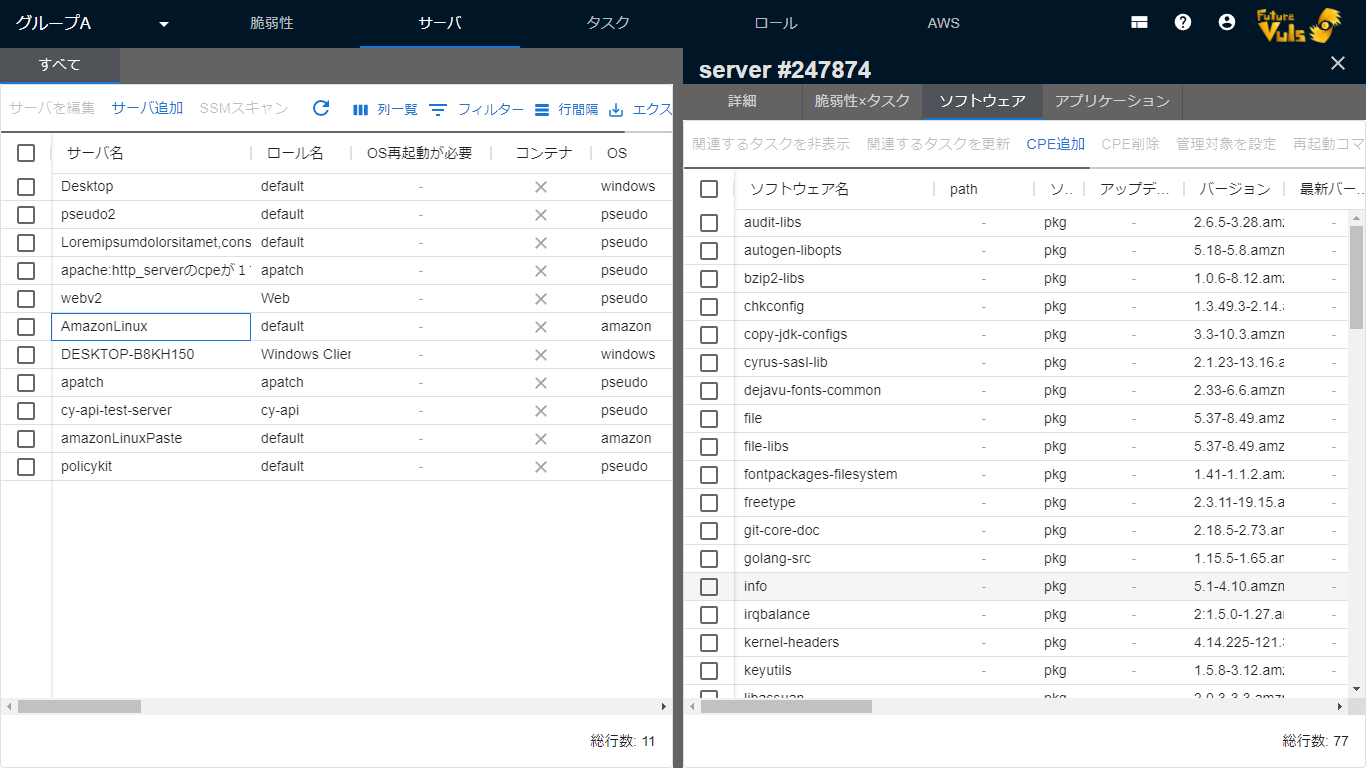
The order and visibility of the items in the list can be set on the screen.
As of May 2022, OSS licenses are detected only for application-dependent libraries. OSS licenses for OS packages are not detected.
| Item | Details |
|---|---|
| Software Name | Display software name or CPE |
| Version | Version of software or CPE |
| Latest Version | When scanning with Vuls scanner in fast-root scan mode, the latest version that can be updated on all Linux is displayed. In the fast scan mode, on some OS (AlmaLinux, Rockey Linux, etc.), the latest version can be obtained without root privilege, so it is displayed. However, it is not displayed in the case of CPE, Paste scan, Offline scan mode, or when the scan target is Windows. |
| OSS License | OSS license of application-dependent libraries |
| Server Name | Display server name where the software is registered |
| Repository | Display the repository managing the software |
| Patch provided | Display whether all patches of the software have been provided or not (displayed only when opened from the vulnerability list). If a vulnerability is detected that cannot be fixed, it will be displayed in red. |
| Additional Information | Additional information of software |
Bulk Update Tasks Related to Software
You can bulk update tasks related to multiple software by selecting the software.
Note that there are different options for bulk updating between software on the server and software under vulnerabilities.
The upper limit of bulk update tasks is 10,000. If you exceed 10,000 tasks, update them multiple times.
When you open software from the server list or role list pane
Only tasks related to the specified software on the specified server will be updated.
When you open software from the vulnerability list pane
The following options are available:
- Update only the tasks related to the selected vulnerability among the tasks of the specified software.
- Update all tasks related to the specified software.
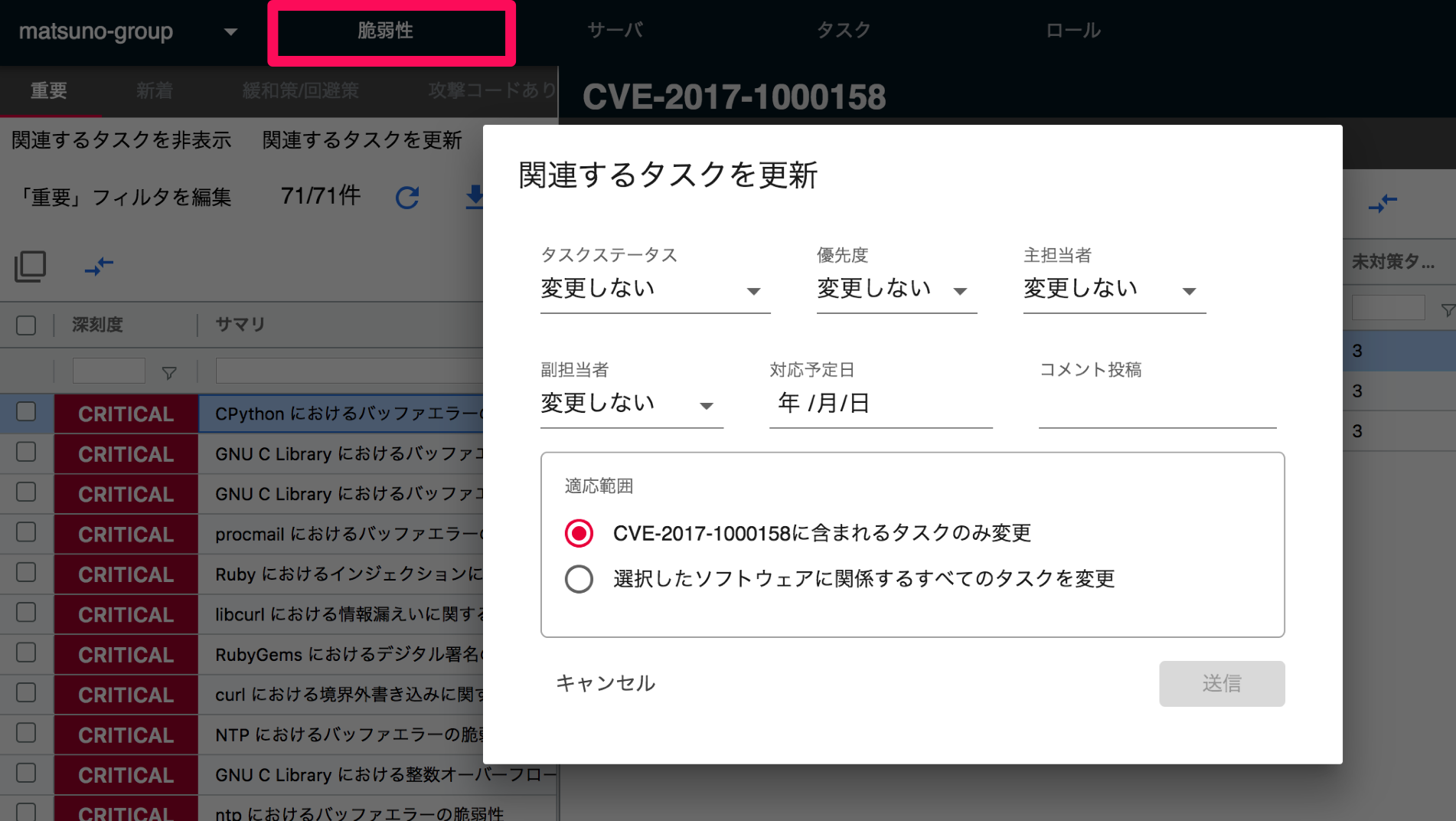
Software Details
You can check and update the details of the software in the Software Details section. The displayed items may vary depending on the type of software.
The following items are displayed in the Software Details section:
| Item | Details |
|---|---|
| Processes that require reboot | Displays the process ID, path, etc. of processes that require reboot. |
| Affected processes | Displays the affected processes. |
| Vulnerabilities and tasks related to software | Displays the CVE-ID and tasks related to the software. |
| Additional Information | Additional information of software |
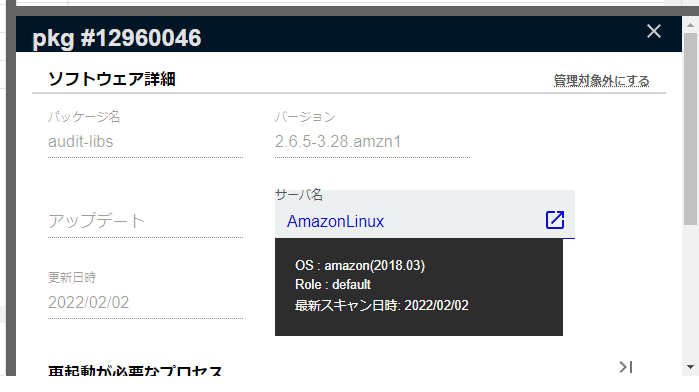
Software Details > OSS License
You can check OSS license information in the Software Details section.
For libraries, OSS license information is collected.
The OSS license information is updated regularly, but it may take up to an hour for the license information to be displayed after scanning the server.
License Information Sources and Reliability
OSS license information is collected from data sources based on the library distribution.
The data sources are as follows:
| Library Type | Data Source |
|---|---|
| Java | https://repo1.maven.org |
| Ruby | https://rubygems.org |
| Python | https://pypi.org |
| Nodejs | https://registry.npmjs.org |
| Go | https://pkg.go.dev |
| Rust | https://crates.io |
-
If license information was collected but the information source could not be obtained,
unknownis displayed. -
Depending on the state of the information source, the reliability of the license information may not be guaranteed. If the reliability is not 100%, a link to the help page will be displayed.
-
If the reliability is not 100%, there are two possible reasons:
- Specific version-based information sources cannot be obtained, so the latest version’s license is obtained instead.
- The information source is not in a defined format, and it is abstractly analyzed using github.com/google/licenseclassifier (this is possible in the case of Java).
AGPL and GPL Licenses
- If the license information is classified as AGPL or GPL, a link to the help page will be displayed.
- When developing services or applications for which it is difficult to disclose source code, it is important to be careful when using libraries that apply these licenses.
- Licenses classified as AGPL or GPL have a characteristic called copyleft, which requires the same license to be applied to secondary works using the library.
- In addition, the license terms include permission to:
- Examine the program’s operation and modify it, and access to its source code for that purpose.
- Redistribute copies of the program.
- Improve the program and release the improvements to the public.
- The main difference between AGPL and GPL is the conditions for applying copyleft and restrictions.
- AGPL-based: Requires the license terms to be applied even for software services provided over a network.
- GPL-based: Requires the license terms to be applied when distributing the software.
- The details and license texts of each license are available on www.gnu.org.
Managed Settings
You can set managed settings for software.

You can set specific software as unmanaged by selecting “Set as Unmanaged” from the menu.
If a new vulnerability is detected in software that has been set as unmanaged, a task will be created as a hidden (“Always Hidden”) task. This does not affect any existing tasks. Hidden tasks can be released from the task details screen.
If there is software that you do not intend to address vulnerabilities for and cannot uninstall, you can set it as unmanaged and always hidden.