Local and Remote Scanning
In order to scan servers for vulnerabilities with FutureVuls, a scanner program must be installed. FutureVuls offers two modes.
-
Local Scan
- Only the server itself, on which the scanner program is installed, will be scanned.
- The installer defaults to local scan.
- Local scan does not require SSH login configuration.
- Only the server itself, on which the scanner program is installed, will be scanned.
-
Remote Scan
- Both Windows and Linux are supported.
- The server where the scanner program is installed is used as the scan execution server, and SSH login to a server connected to the same network is used to perform the scan.
- By adding settings to the configuration file, scanning can be performed without installing the scanner program on each server.
- To login to the server to be scanned via SSH, a user account that can remotely login from the server to be scanned is required.
- Both Windows and Linux are supported.
Local Scan
-
log in to FutureVuls as a user with group administrator privileges and click on the icon in the upper right corner to access “Group Settings” 2.
-
click on “Scanner” from the list on the left. Copy the installation commands as they appear.
FutureVuls requires access to the Internet from the server running the scan during installation and uploading scan results. If your environment requires access to the Internet via a proxy server, please refer to the chapter configuration=>proxy settings and make the necessary settings before performing the following installation.
On the server where the scanner program is to be installed, execute the command copied in “2. At this time, execute the command as a privileged user as follows: For Linux: Execute the command as a privileged user.
- For Linux : Log in as a user who has been granted “root authority
If you get the following message, switch to a user with root privileges and execute again.
2017/11/08 06:04:19 [START ]: chkRootUser
2017/11/08 06:04:19 [ERROR ]: Please run as root user.
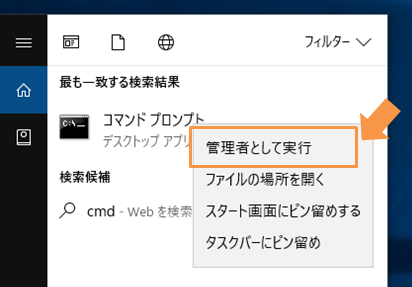
- For Windows : Right click at command prompt startup and start from “Run as administrator”.
-
The installer will perform the following operations.
-
Deploy executable file
- /opt/vuls-saas/vuls
-
Create config file
- /opt/vuls-saas/config.toml
-
Create execution user/group & home folder
- User: vuls-saas
- Group: vuls-saas
-
Registration of periodic execution
- By default, it is set at the time of installation (daily).
- Change as necessary.
- Linux: cron file (/etc/cron.d/vuls-saas-scan)
- Windows: Task scheduler (vuls-saas-scan)
-
Install OS packages required for scanning
- RedHat, OracleLinux, AmazonLinux
- Package name: yum-utils
- Debian
- Package: reboot-notifier
- RedHat, OracleLinux, AmazonLinux
- After installation, when a scheduled run is performed, a scan is automatically performed and the scan results are uploaded to FutureVuls.
FutureVuls requires access to the Internet from the scan execution server during installation and upload of scan results. If your environment requires access to the Internet through a proxy server, you will need to configure the proxy settings after installation. Please refer to the chapter Configuration=>Proxy Settings and make the necessary settings.
Remote Scan
This section describes how to set up remote scanning. The server on which the Scanner is set up is the “Scanner Server”, the The server to be vulnerability scanned is described as “scan target server”.
Preparation on the server to be scanned
Remote scan requires the following settings on the scan target server.
- Install the dependent packages on the scan target server
- Configure /etc/sudoers on the server to be scanned
For local scans, the installer will automatically configure the above, but for remote scans, manual configuration is required.
Install Scanner
Install the scanner program on the scanner server as described above for local scan.
FutureVuls uses SSH login with RSA public key authentication when scanning remote servers (password authentication is not supported). Please have a user who can log in to the remote server, as well as a private key and a public key.
For remote scanning, please make a manual SSH connection from the scanner server to the server to be scanned once in advance. This is to register the host fingerprint of the scanned server in SSH’s known_hosts.
Modify config file
To scan remote servers, add the following configuration to the config file.
- Config file path: /opt/vuls-saas/config.toml
$ vi /opt/vuls-saas/config.toml
[servers]
[servers.localhost]
host = "localhost"
port = "local"
# ↑↑ Local scan settings are automatically configured by the installer ↑↑
# ↓↓ Add the settings of the server to be scanned to your environment. ↓↓
# ex)
[servers.<server name>]
user = "vuls-saas" ←<user name used for remote login>
host = "192.168.0.100" ←<Server to remote login: IP address or name resolvable server name>
port = "22" ←<port number of the remote login destination>
keyPath = "/opt/vuls-saas/vuls-saas.pem" ←<Location of the private key>
~~~~
keyPath is the SSH private key of the server to be scanned. Duplicate content can be omitted by including it in “default”.
[default]
#port = "22"
#user = "username"
#keyPath = "/home/username/.ssh/id_rsa"
For remote scanning of multiple servers
Define multiple servers to be scanned as follows. UUIDs will be generated automatically at report time if not defined.
- Config file path: /opt/vuls-saas/config.toml
[default]
port = "22"
keyPath = "/home/vuls-saas/.ssh/stg.pem"
scanMode = ["fast-root"]
[servers]
[servers.ama2]
user = "ec2-user"
host = "13.113.92.xx"
[servers.ama2.uuids]
ama2 = "xxxxxxxxxxxxxxxxxxxxxxxxx"
[servers.dev]
user = "ubuntu"
host = "54.248.62.xx"
[servers.dev.uuids]
dev = "zzzzzzzzzzzzzzzzzzzzzzzzzz"
If you specify your own UUIDs, be careful not to duplicate those defined elsewhere in config.toml. FutureVuls uses UUIDs to identify servers. Please note that if the UUID is the same due to a definition error, it will be recognized as the same server.
To remotely scan all servers in range at once by specifying a CIDR range
By specifying a CIDR range in the configuration file, remote scanning can be performed on all servers within the range. Define as follows.
- Config file path: /opt/vuls-saas/config.toml
[default]
port = "22"
scanMode = ["fast-root"]
[servers]
[servers.testNW-target]
user = "ec2-user"
host = "192.168.0.60/31"
keyPath = "/home/vuls-saas/.ssh/auth.pem"
When the scan is performed, the scanner will attempt a remote scan against all IP addresses in the specified range and overwrite them with configuration information for each server if successful.
- Config file after scan.
[default]
port = "22"
scanMode = ["fast-root"]
[servers]
[servers."testNW-target(192.168.0.60)"]
user = "ec2-user"
host = "192.168.0.60"
keyPath = "/home/vuls-saas/.ssh/auth.pem"
[servers."testNW-target(192.168.0.60)".uuids]
"testNW-target(192.168.0.60)" = "bab806a2-59b7-628f-ff6b-c620df7191ca"
[servers."testNW-target(192.168.0.61)"]
user = "ec2-user"
host = "192.168.0.61"
keyPath = "/home/vuls-saas/.ssh/auth.pem"
[servers."testNW-target(192.168.0.61)".uuids]
"testNW-target(192.168.0.61)" = "dbad42bd-f045-5485-1189-f6a6e4d09a01"
For the second and subsequent scans, a remote scan is performed on each server based on the information in the configuration file.
- If the scan fails for any server in the specified CIDR range, the process will be aborted and the configuration file will not be updated.
- If a server in the specified CIDR range has already been configured for remote scan and a UUID has been issued, it will be overwritten with the new UUID after the scan and managed as a different server in FutureVuls.
- If the UUID has been rewritten, please edit the configuration file (
/opt/vuls-saas/config.toml) directly to restore the original UUID - The UUID can be found in the server tab > server details page of the FutureVuls console.
- If the UUID has been rewritten, please edit the configuration file (
How to specify a specific server for remote scanning
- Change /opt/vuls-saas/vuls-saas.sh as follows
$ su - vuls-saas
$ cd /opt/vuls-saas
$ cp vuls-saas.sh vuls-saas.sh.bak
$ vim vuls-saas.sh
$ diff vuls-saas.sh*
diff vuls-saas.sh*
16c16
< ./vuls scan -ips ${@} > scan.log 2>&1
---
> ./vuls scan -ips > scan.log 2>&1
- Perform a scan of a specific server (assuming the two ama2, dev machines in the previous section are defined)
./vuls-saas.sh dev
- To scan multiple servers, specify server names (xxx in [servers.xxx] in config.toml) separated by spaces.
./vuls-saas.sh dev ama2
- To scan all servers defined in config.toml
./vuls-saas.sh