Task
About tasks
Tasks are tickets used to manage vulnerabilities detected by server scans.
Tasks cannot be manually created or closed in order to ensure that only vulnerabilities that have actually been detected are managed.
If a vulnerability is detected during a server scan, a task is added, and if the vulnerability has been resolved, the task is closed (PATCH_APPLIED).
Tasks, vulnerabilities, servers, and roles

| Name | Description |
|---|---|
| Task | Registers “1 server x 1 vulnerability” as 1 task (similar to a ticket) |
| Vulnerability | Manages a list and details of detected vulnerabilities (CVEs) |
| Server | Manages a list and details of scanned servers |
| Role | Manages servers by grouping them |
Tasks cannot be manually registered. They are automatically generated based on vulnerabilities detected on the server.
Status
Tasks have five available statuses:
| Status Name | State | Note |
|---|---|---|
| NEW | Newly detected vulnerability | Set when a vulnerability is detected |
| INVESTIGATING | Under investigation | Set during vulnerability investigation |
| ONGOING | In progress | Set after investigation is complete and while considering and preparing a response |
| DEFER | Task on hold | Set when a response is postponed, such as during regular maintenance |
| WORKAROUND | Mitigated | Set after implementing a workaround, such as a virtual patch or configuration change |
| NOT_AFFECTED | No impact | Set when it is confirmed that the vulnerability does not affect the environment |
| RISK_ACCEPTED | Risk accepted | Set when a decision is made to tolerate the impact of the vulnerability |
| PATCH_APPLIED | Patch applied | Automatically set after the next scan following patch applicationManually setting the status is not allowed |
The status of a task typically transitions as follows:
- Investigate, prepare, and apply a patch
- NEW → INVESTIGATING → ONGOING (preparing to apply patch) → PATCH_APPLIED
- Implement a workaround without applying a patch
- NEW → INVESTIGATING → ONGOING → WORKAROUND → Set to hidden
- Implement a temporary workaround and later apply a patch
- NEW → INVESTIGATING → ONGOING (preparing workaround) → WORKAROUND (workaround implemented) → ONGOING (preparing to apply patch) → PATCH_APPLIED
- Determine that the vulnerability does not affect the environment after investigation…
You can automatically obtain a list of installed WordPress core, plugins, and themes on the server and detect vulnerabilities.
| Item | Details | Update Timing |
|---|---|---|
| Task ID | ID of the task. | None |
| CVE ID | CVE-ID of the task. | None |
| Server name | Name of the task server. | When updating the server |
| Role name | Role name of the server. | When updating the server |
| Server UUID | UUID of the server. | None |
| Task priority | Priority of the task set by the user.Value can be HIGH / MEDIUM / LOW, default is NONE. |
When updating the task |
| Status | Status of the task.Values can be NEW / ONGOING / INVESTIGATING / WORKAROUND / RISK_ACCEPTED / PATCH_APPLIED/ PATCH_APPLIED.NEW / PATCH_APPLIED are automatically set statuses.The user cannot manually set PATCH_APPLIED. |
When updating the task |
| Primary assignee | Primary assignee of the task.Displays the primary assignee set by the user.If the default assignee is set on the server, it will be set when the task is created. | When updating the task |
| Secondary assignee | Secondary assignee of the task.Displays the secondary assignee set by the user. | When updating the task |
| Planned response date | Planned response date of the task.Displays the planned response date set by the user. | When updating the task |
| Response deadline | Response deadline of the task.Displays the response deadline set by the user or set by the caution tag. | When updating the task, updating the caution tag |
| Patch provision | Whether a patch has been provided for the vulnerable software related to the task.✓: Valid patches have been released for all related software.☓: No patches have been provided for all related software at this time.Detailed information is reflected in the Patch provision status.△: Among multiple related software, patches have been provided and not provided.❔: Some related software has an unknown patch provision status.-:Patch applied and vulnerabilities resolved for all related software.If you scan AlmaLinux, or Rocky Linux with fast scan mode or paste scan, you cannot determine whether patches are provided or not, so it is displayed as “❔” (in fast-root scan mode, it is displayed as “○☓△”). |
When scanning |
| Patch provision status | Patch provision status for packages related to tasks. Patch provision status published by each vendor. Example for Red Hat systems (Reference URL) - Will not fix: Vendors judge that they will not provide patches. - Affected: Patch not provided - Fix deferred: Patch will be provided. |
During scan |
| Process running | Whether related processes are running on the server and opening and listening on ports. - Mark, such as media player pause: Process is stopped. - Mark, such as play button: Process is running, but no ports are listening. - Mark, such as radio wave: Process is running, and ports are listening. |
During scan |
| Critical filter | Whether the task meets the criteria for critical unresolved issues. | Upon updating the critical filter. |
| Danger | Whether the task is associated with vulnerabilities that have the Danger flag set. | Upon updating the Danger flag. |
| Attack code available | Whether attack code or proof-of-concept for vulnerabilities associated with the task is publicly available. | Upon changes to DB information. |
| Mitigation/avoidance measures | Whether mitigation or avoidance measures are available from Red Hat or Microsoft data sources. | Upon changes to DB information. |
| Alert information | Whether alert information is published by CISA-KEV, JPCERT/CC-Alerts, or US-CERT-Alerts. CISA-KEV: “Alert information exists (critical)”. JPCERT/CC-Alerts or US-CERT-Alerts: “Alert information exists (notice)”. |
Upon changes to DB information. |
| CloudOne status | CloudOne integration status. | During scan |
| Advisory ID | The advisory ID associated with the vulnerability is displayed. (For Windows, this is the KBID.) | Upon changes to DB information. |
| Alert tag | The special alert tag registered with the vulnerability. | Upon updating the alert tag. |
| Confidence level | Displays the confidence level of the detection method or information source. | During scan |
| Vulnerable software | Displays packages related to the task. Only displays packages with remaining vulnerabilities. |
During scan |
| Server tag | Tags set for the server associated with the task. | Upon updating the server. |
| SSM integration | AWS SSM integration status. | During scan |
| SSVC PRIORITY | SSVC priority. | During scan |
| Update date and time | The date and time the task was last updated. | During scan, upon updating the task. |
| Initial detection date and time | The date and time the vulnerability associated with the task was first detected. | During scan, upon updating the task. |
| Hide flag | Hide flag status of the task. If the task is set to be hidden, “○” will be displayed. | During scanning, updating hidden tasks |
| Hide type | Conditions for hiding. | During scanning, updating hidden tasks |
| External Scan | Whether any vulnerabilities tied to the task are exposed to the outside world | When [add and update external scan result](/en/manual/scanimport/#Adding External Scan Results)) |
Subtabs
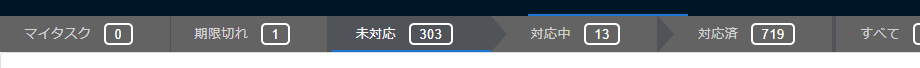
Tabs are provided for ease of use in the task list.
| Tab name | Tasks to be obtained |
|---|---|
| Not yet handled | List of tasks with NEW status and not set to be hidden |
| My task | List of tasks where you are assigned as the main or sub responsible party and have not been handled |
| Handling | List of tasks with INVESTIGATING or ONGOING status and not set to be hidden |
| On hold | List of tasks with DEFER status and not set to be hidden |
| Expired | List of tasks where the handling deadline has passed and have not been handled |
| Handled | List of tasks with status WORKAROUND or PATCH_APPLIED or set to be hidden |
| All | List of all tasks |
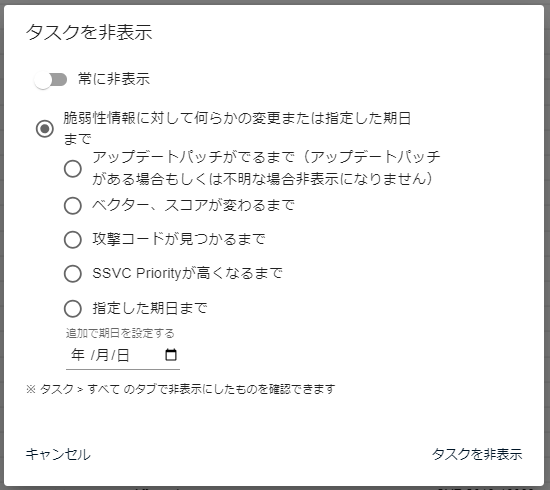
Hide specified tasks in bulk
The upper limit of bulk task update is 10,000 tasks. If you have more than 10,000 tasks, please update them in multiple times.
Select multiple tasks to hide them.
Update specified tasks in bulk
The upper limit of bulk task update is 10,000 tasks. If you have more than 10,000 tasks, please update them in multiple times.
You can update multiple selected tasks in bulk.
SSM Update
You can issue an on-demand update command for vulnerabilities on EC2 instances that have registered AWS authentication information.
Update command
Select one or more tasks to display the update command.
The update command appropriate for each server OS will be displayed.
However, no update commands will be displayed for packages registered with CPE.
Ansible
Select multiple tasks to display the appropriate Ansible Playbook for each server OS.
However, no update commands will be displayed for packages registered with CPE.
Task Second Pane
When you click on an item in the task list in the first pane, the second pane appears. In the Detail tab, you can check and update task details.
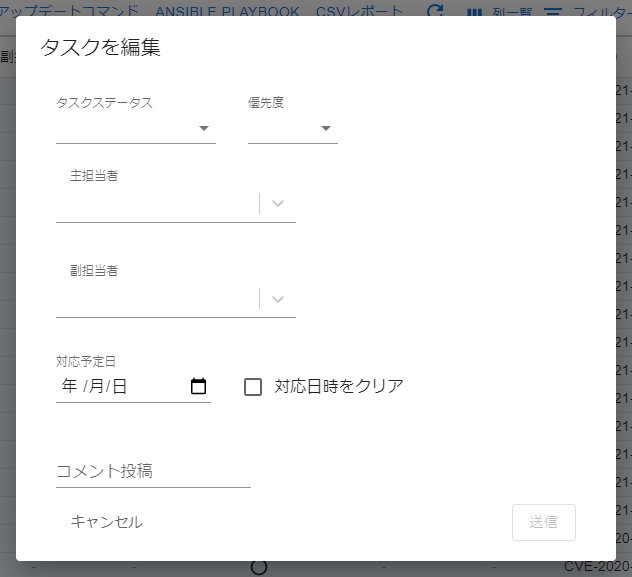
Task Update
The following items can be set in Task Update:

| Item | Details |
|---|---|
| Task priority | The priority of the task set by the user will be displayed. Value is HIGH / MEDIUM / LOW. Default is NONE. |
| Status | The task’s status is displayed. Value is NEW / ONGOING / INVESTIGATING / DEFER / WORKAROUND / NOT_AFFECTED / RISK_ACCEPTED / PATCH_APPLIED. The status automatically set is NEW / PATCH_APPLIED. The user cannot manually set PATCH_APPLIED. |
| Scheduled completion date | The scheduled completion date of the task. Displays the scheduled completion date set by the user. |
| Deadline | The deadline for the task. Displays the deadline set by the user or the deadline set by the alert tag. |
| Main person in charge | The main person in charge of the task will be displayed. The main person in charge set by the user will be displayed. If a default person in charge is set for the server, the default person in charge will be set when the task is created. |
| Subordinate person in charge | The subordinate person in charge of the task will be displayed. The subordinate person in charge set by the user will be displayed. |
| Comment | The comments posted on the task are displayed. Can be written in Markdown format. |
Task Hide Setting
You can use the hide flag in the upper right corner of the task details to hide the task.
By using hiding, it is possible to perform more efficient vulnerability management.
Related software
You can check the software with vulnerabilities associated with the task.
| Item | Details |
|---|---|
| Software Name | Vulnerable Software Name |
| Version | Current version of the installed software |
| Update | Latest version of the software |
| Path | Path to the definition file of the language library |
| Repository | Software repository |
| Patch Offer Status | Status and version of the patch if available |
| Initial Detection Date | Date and time when the software was first detected |
| Affected Processes | Information on affected processes |
In addition, if a patch is available, you can use the Update Command Function.
Related Advisories
You can check a list of advisories related to the vulnerability that the task is associated with and links to their pages.

Related External Scan Results
You can check a list of external Scan results associated with the task and a link to the page
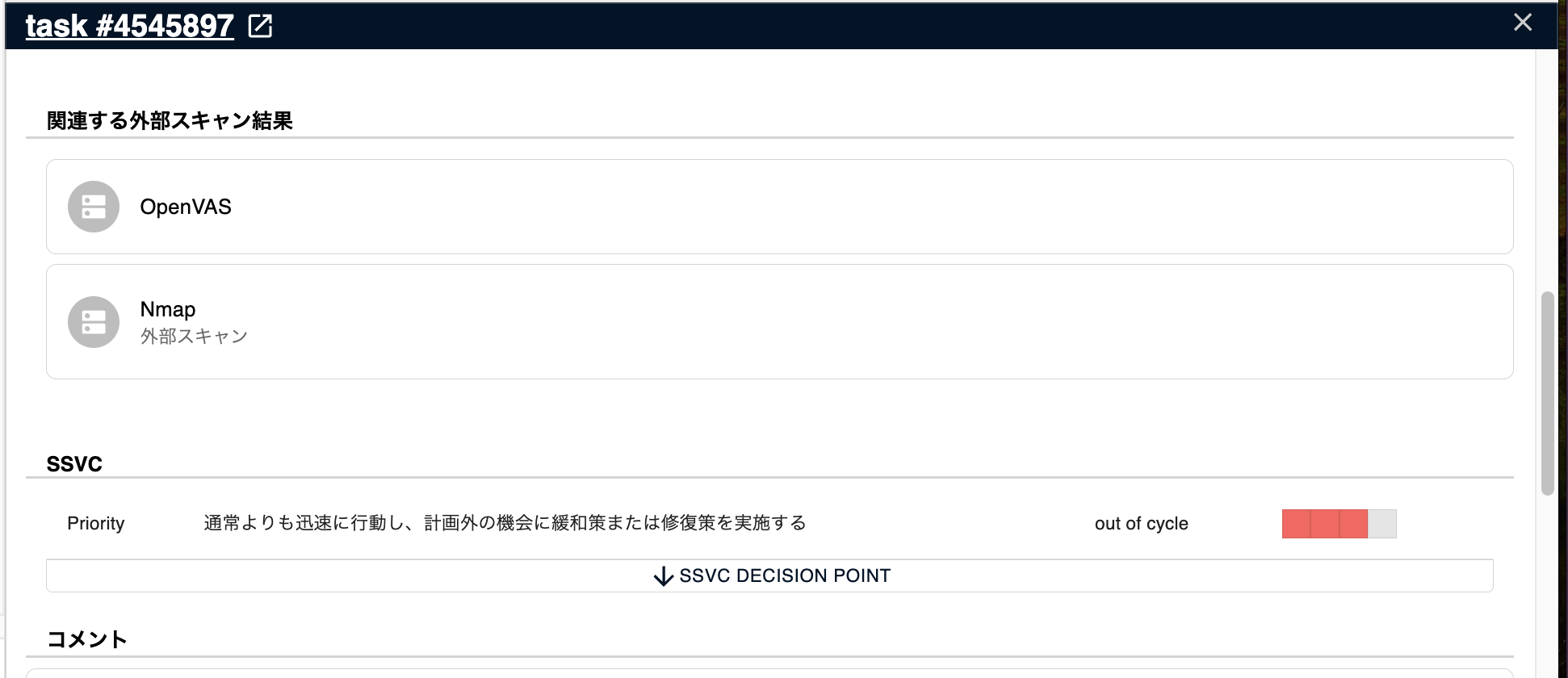
SSVC
This feature is only available for the CSIRT plan.
You can check the SSVC priority of the task and the reasons for its derivation in SSVC.

Comments
You can check the task’s update history by the system and post comments to share information with other users.
You can switch the display setting of the system update history with the Display system update history bar.
Notification of Comments by Mention
Mentions can also be made in comments.
By entering @ and selecting the target, the user will be notified by e-mail of the task contents.
You can select a target from each user name and user group.
[Mention candidates displayed on the group screen]
- Individual users with the following privileges (can be confirmed at
Group Settings > Members)- Owner
- CSIRT
- Group set administrator / member
- Group administrator / member
- User groups with specific privileges
- Owner (
@owner) - CSIRT (
@csirts) - Administrator (
@groupSetAdmin) / Member (@groupSetMember) of the group set containing the group to which the relevant task belongs - Administrator (
@groupAdmin) / member (@groupMember) of the group to which the relevant task belongs
- Owner (
[Mention candidates on the Group Set screen]
- Individual users with the following privileges (can be confirmed at
GroupSetSettings > Members)- Owner
- CSIRT
- Groupset administrator / member
- User group with specific privileges
- Owner (
@owner) - CSIRT (
@csirts) - Administrator (
@groupSetAdmin) / Member (@groupSetMember) of the group set containing the group to which the relevant task belongs - Administrator (
@groupAdmin) / member (@groupMember) of the group to which the relevant task belongs
- Owner (